Technology
Prove facts, without disclosing any data.
We're combining Zero Knowledge Proofs with Blockchain immutability + quantum resistant cryptography with our ZK execution engine (ZKXE).
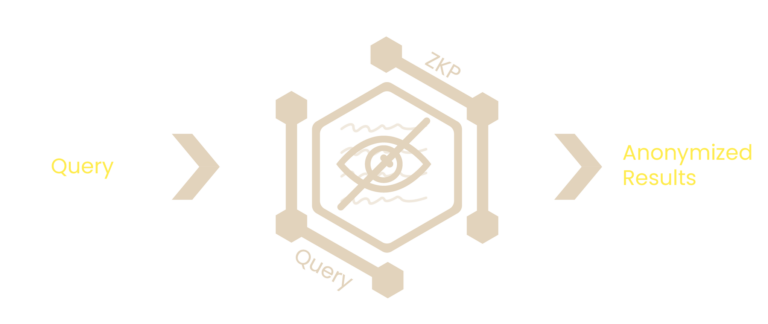
You can ask complex questions about private data and anonymise the results or return action results.


Technology
Prove facts, without disclosing any data.
We're combining Zero Knowledge Proofs with Blockchain immutability + quantum resistant cryptography with our ZK execution engine (ZKXE).
You can ask complex questions about private data and anonymise the results or return action results.
Technologies
zkQuery
Work with complex data types, rich text functionality & aggregate functions. Use “SQL as JSON” powered by proprietary SQL ZKXE.
zkReceipt
Secure storage of personally identifiable information (PII) within blockchain transactions, without disclosing private information.
Asset Trading
Transfer an unlimited volume of digital product between 2 parties instantly. Sensitive materials are never revealed on the blockchain,
Quantum-Resistant Blockchain storage
Immutable data, stored on the blockchain cannot be tampered with. Your solution can now leverage Arweave to guarantee Immutablility.
Data Monetization
Sovereign users can allow zkQuery execution. They receive rewards for executing zkQueries.
Clear Carbon
Clear Carbon is a software implementaion of the transparent workflow of carbon offset production, through to sale process.
Public API
Over 30 million developers use Postman. Simplify the process of testing the Tau Oracle APIs, simply use Postman
Omnitechture
The move from monolith to cloud was gradual, so we have architected for gradual migration of corporate landscapes to blockchain.
How to interact with PII and maintain privacy
zkQuery
ZKXE - zk Execution Engine
A zero-knowledge proof is a way for one party to demonstrate the truth of a statement to another party without revealing any additional information beyond the statement itself.
A zero-knowledge proof is a way for one party to demonstrate the truth of a statement to another party without revealing any additional information beyond the statement itself.
Tau allows your dApp to execute query logic against encrypted Tau data and return a result.
Clear statements are SQL always vulnerable to injections, which is why we have built a structure of “SQL as JSON”

The next evolution of the sales slip.

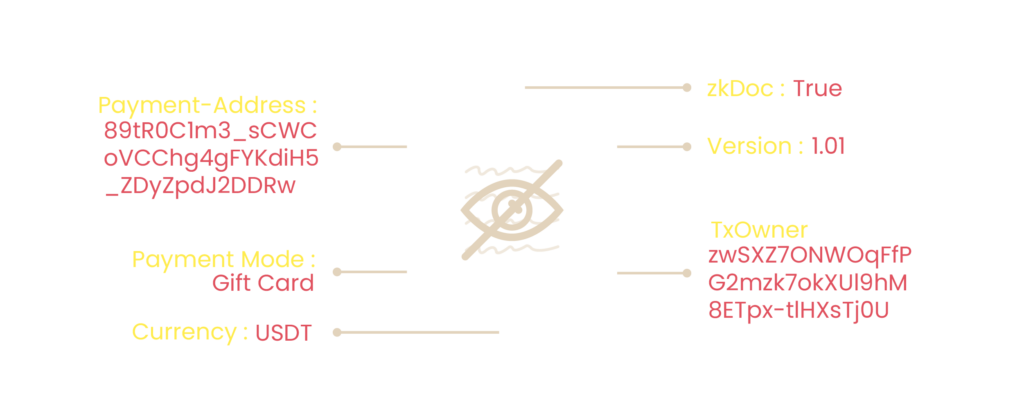
zkReceipt
Privacy you can validate
zkReceipt's are essentially a branded zkBox.
zkBoxes technology enables secure storage of personally identifiable information (PII) within blockchain transactions. With the owner's permission, inquiries can be made about the transaction's contents without disclosing private information.
This allows for permanent access to purchase receipts via blockchain. Imagine having all your sales slips immutably in one place, consumer returns procedures would be closer to frictionless. With a buyers permission, the merchant can validate a purchase.
zkReceipt
Privacy you can validate
zkReceipt's are essentially a branded zkBox.
zkBoxes technology enables secure storage of personally identifiable information (PII) within blockchain transactions. With the owner's permission, inquiries can be made about the transaction's contents without disclosing private information.
This allows for permanent access to purchase receipts via blockchain. Imagine having all your sales slips immutably in one place, consumer returns procedures would be closer to frictionless. With a buyers permission, the merchant can validate a purchase.



Trade private assets stored on-chain
Asset Trading
Preserving data privacy
Designed for freelancers & online auction houses working in the blockchain space, Tau brings you the ability to transfer an unlimited volume of digital product between 2 parties instantly.
You dApp can now transfer digital product securely, the contents remain private, and is never revealed to the blockchain.
The ownership or license is transfered, sensitive materials are never revealed on the blockchain, only ownership is exposed.




Future proof, permanent forensic cold storage
Decentralized, Immutable Storage
Quantum-Resistant Blockchain storage
All cloud storage providers suffer from the same weakens, data can be modified by at least 1 person.
Immutable data, stored on the blockchain cannot be tampered with.
Existing data security models are not built to resist quantum computers, permanent blockchain storage project’s need Quantum Resistant Cryptography.
This is a ticking time bomb in data privacy.
Decentralized, Immutable Storage
Quantum-Resistant Blockchain Storage
All cloud storage providers suffer from the same weakens, data can be modified by at least 1 person.
Immutable data, stored on the blockchain cannot be tampered with.
Existing data security models are not built to resist quantum computers, permanent blockchain storage project’s need Quantum Resistant Cryptography.
This is a ticking time bomb in data privacy.
How can you monetize sensitive data, and maintain trust?
ZK Data Monetization
ZK Data Anonymisation
Sovereign users, own their data.
Only they can decrypt it.
Sovereign users can allow ZKP Query execution.
They receive rewards for executing ZKP queries.
ZKP queries produce licenced anonymized behavioral data.
Leavarge to power of “SQL as JSON”
ZK Data Monetization
ZK Data Anonymisation
Sovereign users, own their data.
Only they can decrypt it.
Sovereign users can allow ZKP Query execution.
They receive rewards for executing ZKP queries.
ZKP queries produce licenced anonymized behavioral data.
Leavarge to power of “SQL as JSON”

Putting the trust into the VCC purchases for blockchain transactions
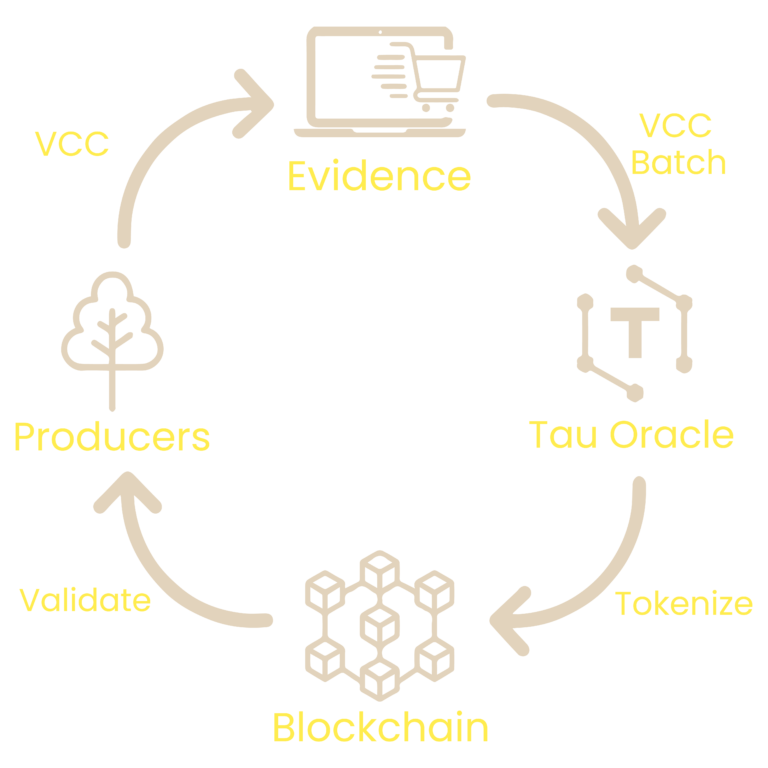
Clear Carbon
Anti-Greenwashing on Blockchain
Clear Carbon is a software implementaion of the transparent workflow of carbon offset production, through to sale process.
It protects buyers & producers from “double counting” by using zkReceipts.
Carbon usage is tracked on the blockchain on the transaction.
Buyers can choose to buy VCC from projects which align with them both commercially and personally.
Clear Carbon
Anti-Greenwashing on Blockchain
Clear Carbon is a software implementaion of the transparent workflow of carbon offset production, through to sale process.
It protects buyers & producers from “double counting” by using zkReceipts.
Carbon usage is tracked on the blockchain on the transaction.
Buyers can choose to buy VCC from projects which align with them both commercially and personally.

Connect from anywhere
Public API
Simplify onboarding with Postman
Postman is an API platform for building and using APIs. Postman simplifies each step of the API lifecycle and streamlines collaboration
Over 30 million developers use Postman.
Simplify the process of testing the Tau Oracle APIs, simply use Postman


Built with RFP’s in mind

Omnitechture
Slowly migrate to Web3
The Vision for Tau is to become the infrastructure that unites all technology.
All technology solutions rely on data, whether for storage or interaction.
Tau aims to be the fabric that seamlessly integrates it all.
Omnitechture
Slowly migrate to Web3
The Vision for Tau is to become the infrastructure that unites all technology.
All technology solutions rely on data, whether for storage or interaction.
Tau aims to be the fabric that seamlessly integrates it all.

Topology